• TCP 기본 포트 스캔
┌──(root㉿kali)-[~]
└─# nmap 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:37 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00018s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.23 seconds
• TCP 하프 연결을 이용해서 Stealth 모드로 스캔한다.
┌──(root㉿kali)-[~]
└─# nmap -sS 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:38 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00017s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.27 seconds
• 열려 있는 포트, 서비스 이름, 버전, OS 정보
┌──(root㉿kali)-[~]
└─# nmap -sS -sV -O 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:40 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00028s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.2
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.6 ((CentOS))
MAC Address: 00:0C:29:1C:13:CE (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14
Network Distance: 1 hop
Service Info: OS: Unix
OS and Service detection performed. Please report any incorrect results at https ://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.81 seconds
• UDP 스캔
┌──(root㉿kali)-[~]
└─# nmap -sU 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 03:11 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00035s latency).
All 1000 scanned ports on 192.168.11.17 are in ignored states.
Not shown: 1000 closed udp ports (port-unreach)
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1087.49 seconds
• UDP 포트 53(DNS), 161(SNMP) 탐지
┌──(root㉿kali)-[~]
└─# nmap -sU -p 53, 161 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:44 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00032s latency).
PORT STATE SERVICE
53/udp closed domain
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap done: 2 IP addresses (1 host up) scanned in 3.31 seconds
ㄴ snmp는 서버를 설치하지않아서 아에 안뜸.
• ICMP(ping) 또는 ARP로 응답하는 IP만 확인
┌──(root㉿kali)-[~]
└─# nmap -sn 192.168.11.0/24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:47 EDT
Nmap scan report for 192.168.11.1
Host is up (0.00012s latency).
MAC Address: 00:50:56:F3:BF:C8 (VMware)
Nmap scan report for 192.168.11.3
Host is up (0.011s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.11.17
Host is up (0.00020s latency).
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap scan report for 192.168.11.205
Host is up (0.00018s latency).
MAC Address: 00:0C:29:63:9F:D0 (VMware)
Nmap scan report for 192.168.11.254
Host is up (0.000097s latency).
MAC Address: 00:50:56:EA:03:E3 (VMware)
Nmap scan report for 192.168.11.36
Host is up.
Nmap done: 256 IP addresses (6 hosts up) scanned in 2.09 seconds
# nmap 192.168.11.1 192.168.11.20
┌──(root㉿kali)-[~]
└─# nmap 192.168.11.1 192.168.11.20
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:48 EDT
Nmap scan report for 192.168.11.1
Host is up (0.000082s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:F3:BF:C8 (VMware)
Nmap done: 2 IP addresses (1 host up) scanned in 1.41 seconds
• 여러 대상에 대한 스캔
┌──(root㉿kali)-[~]
└─# nmap 192.168.11.1-20
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:49 EDT
Nmap scan report for 192.168.11.1
Host is up (0.00011s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE
53/tcp open domain
MAC Address: 00:50:56:F3:BF:C8 (VMware)
Nmap scan report for 192.168.11.3
Host is up (0.0075s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.11.17
Host is up (0.00018s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:1C:13:CE (VMware)
Nmap done: 20 IP addresses (3 hosts up) scanned in 5.92 seconds
• 웹 서비스 탐지
┌──(root㉿kali)-[~]
└─# nmap -p 80,443 -sV 192.168.11.17
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-12 02:50 EDT
Nmap scan report for 192.168.11.17
Host is up (0.00032s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.6 ((CentOS))
443/tcp closed https
MAC Address: 00:0C:29:1C:13:CE (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.38 seconds
nmap -sN 192.168.11.17

00 0c 29 1c 13 ce 00 0c 29 c6 9f c0 08 00 45 00
00 28 8e 56 00 00 38 06 5c f4 c0 a8 0b 24 c0 a8
0b 11 b5 40 00 c7 89 63 2c 16 00 00 00 00 50 00
04 00 a8 dd 00 00 00 00 00 00 00 00
보낸 쪽 tcp 헤더쪽을 보면 flag 쪽에 전부 not set으로 되어있다.
그래서 닫힌 포트기 때문에 내용이 없는 패킷이기 때문아리서 rst 패킷을 보내는걸 확인할수 있습니다.
nmap -sX 192.168.11.17
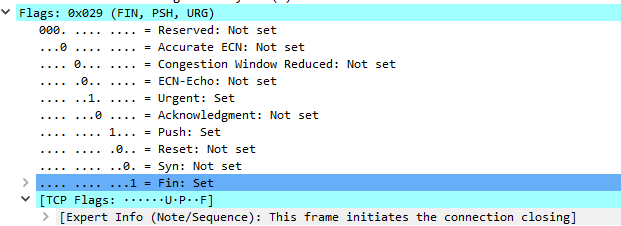
00 0c 29 1c 13 ce 00 0c 29 c6 9f c0 08 00 45 00
00 28 6b 90 00 00 3a 06 7d ba c0 a8 0b 24 c0 a8
0b 11 fd 45 06 bb 28 84 99 66 00 00 00 00 50 29
04 00 4e 4a 00 00 00 00 00 00 00 00
보낸쪽 tcp 헤더쪽 flag를 확인해보면 fin , push, urgent 쪽만 set으로 되어있다.
그래서 닫힌 포트에서는 논리적으로 함께 사용될수 없는 플래그를 요청한거기때문에 rst패킷을 보낸다.
둘다 닫힌 포트에서 rst패킷을 보내지만 -sN는 텅빈 패킷을 보내는 것이고, -sX는 모순되는 패킷을 보내는걸로 알수있다.
그리고 rst 패킷을 보내는 애들은 닫힌 포트라고 알수있다. 왜냐면 포트가 열려있으면 반응을 안하기 때문.